1. Smart Home
Room #1:
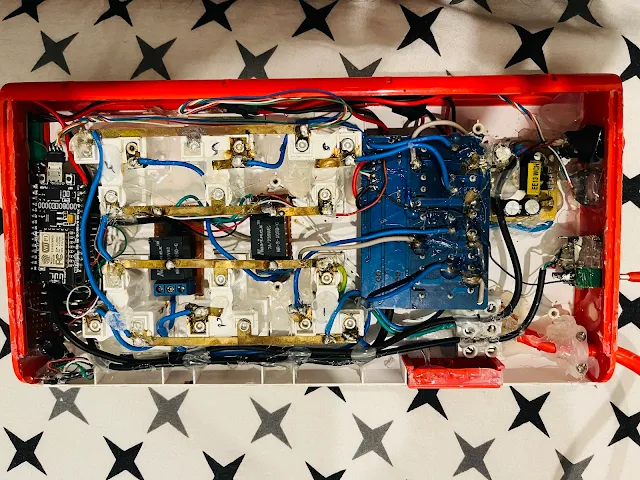
In this room, I have implemented an automation system using an 8-channel relay, a NodeMCU ESP8266, and an AC to DC 5V 2A adapter board, all neatly housed inside a large box. This setup is connected to the tube lights, ceiling fan, Philips Wiz smart LED Bulb (10W), DIY RGB lamp (RGB Strip, ESP8266), study lamp, and three 2-pin sockets, which I use to plug devices like phone chargers and laptops. I've automated these sockets to turn off at a specific time when the device reaches 100% charge, ensuring devices don't overcharge, which is safer. I can safely leave them plugged in overnight without worrying about overcharging!
For AC control, I use a Homemate Wi-Fi IR remote (I tried DIY in past, not reliable and its limited), which allows me to turn the AC on/off, change modes, set the temperature, and more, either via its app or with voice commands through Alexa and Google Assistant. I've also automated the AC to maintain a temperature of 24°C until 3 AM, then increase to 26°C until 5 AM before turning off. The fan is programmed to turn off at 6 AM, helping me wake up on time while saving power. The lights can also be automated to turn on during this schedule, but I’ve left this option as a backup.
Room #2:
This room is equipped with a Philips Wiz smart LED Bulb (10W), which is used both as a normal light and a night lamp (lighting at just 10% brightness in night mode). I've connected a 40A Solid State Relay (SSR) and a NodeMCU ESP8266 inside the AC stabilizer to control the AC unit's power. I’ve also created a DIY SSR relay using a 3W LED and Light Dependent Resistor (LDR) to manage the AC control via the stabilizer. The ESP8266 inside the stabilizer is programmed with Tasmota, allowing control via an app or through Alexa/Google Assistant. I've automated the AC to turn on until 5 AM, after which the unit turns off, followed by the stabilizer 5 minutes later. This helps me wake up naturally while saving energy. The light can also be automated to turn on at a specific time, though this feature remains optional.
Living Room #3:
In the living room, I use an Echo Dot 3rd Gen for voice control. A 4-channel relay, NodeMCU ESP8266, and an AC to DC 5V 1A adapter are housed in a box to manage the connected devices, which include the TV, TV lights (LED strip behind the TV), and 5.1 soundbar home theater system. The devices are integrated with Sinric Pro, which allows for Alexa and Google Assistant compatibility via its app and web dashboard (free for up to 3 devices).
Automation in this room is configured as follows:
When I say, "Alexa, turn on TV," the TV turns on.
When I say, "Alexa, movie time," the TV turns on (if off), the soundbar turns on and connects automatically to the TV via HDMI ARC, TV lights turn on, and the Philips Wiz LED bulb in the living room turns off, creating the perfect movie ambiance.
For "Alexa, movie break," the soundbar (via Homemate Wi-Fi IR remote) pauses the TV/media, and the Wiz light turns on to 50%, allowing for a quick break before resuming the movie.
Everything in the living room is customized using the Alexa app, allowing for seamless control and communication with all connected devices in one place.
Kitchen #4:
The kitchen automation includes a water pump motor timer using a 40A SSR and an Arduino Nano. I programmed the timer using simple Arduino code with 3 buttons: a 2-minute option (when unsure about the water tank level), a 7-minute option (when the tank is empty and needs to be filled), and a reset button to stop the pump or change the timer. The setup is powered by an AC to DC 5V 1A adapter and housed in a 2-module electrical box, wired to the existing motor switch. This system ensures efficient water usage, preventing overflows and saving energy. I can also connect a NodeMCU ESP8266 to enable control via a mobile app, Alexa, or Google Assistant from anywhere, but in this case its not necessary.
2. Smart Extension Box V3
The extension box now has individual control switches thanks to an IR receiver module (TSOP) and a small generic IR remote. I extracted the IR values and assigned them to each of the six sockets, using the '0' button to turn off all sockets at once. The box can also be controlled via the ESP RainMaker app, Alexa, or Google Assistant, allowing for timers and automation.
3. Bike Keyless Entry via IoT
For added fun, I also connected the high beam light switch and horn switch (as a car unlock method), but these are limited due to Sinric Pro’s 3-device limitation. The bike can be controlled via Alexa and Google Assistant. I’ve DIYed a Bluetooth receiver into my helmet, allowing me to turn on the bike while wearing it, giving me a Tony Stark/Iron Man-like experience!
Additionally, I installed an RF module salvaged from an old RC car, which I transformed into a remote keychain. This makes the bike fully keyless—automatically unlocking when I’m near and locking when I move more than 10 meters away. Since I’m usually out and about, I activate my phone’s mobile hotspot (with the same SSID as my home network) to make the system work, although Bluetooth is another option with more limited range.
I can also control the system via the Alexa app on my WearOS watch for a futuristic touch!
4. WiFi Deauther and WiFi Duck: Making, Testing, and Understanding the Technology
Parts Used:
Pro Micro (Atmega 32u4): A microcontroller board capable of emulating a USB HID device, such as a keyboard or mouse.
https://robu.in/product/pro-micro-5v-16m-mini-leonardo-micro-controller-development-board-for-arduino/
OLED Display (0.96 inch): A small screen that displays the status and actions of the device.
https://robu.in/product/0-96-inch-yellow-yellow-blue-oled-lcd-led-display-module/
D1 Mini (ESP8266): A WiFi-enabled microcontroller, which enables both the deauthentication attacks and hotspot capabilities for the WiFi Duck.
https://robu.in/product/d1-mini-v2-nodemcu-4m-bytes-lua-wifi-internet-of-things-development-board-based-esp8266/
ESP8266 Antenna: Provides better signal range and stability for WiFi-based attacks.
https://robu.in/product/esp-8266-esp8266-serial-wifi-wireless-transmitter-module-gain-antenna-mt76813dbi/
Battery Charging Module (TP4056): Ensures the device can be portable by allowing a battery to charge and power the project.
https://robu.in/product/tp4056-1a-li-ion-lithium-battery-charging-module-with-current-protection-type-c/
RGB LED Module: Adds visual feedback through colors, indicating different states of the device.
https://robu.in/product/cjmcu-123-ws2811-rgb-led-breakout-module/
Micro Switch (KW10): A simple switch to control various functions.
https://robu.in/product/microswitch-kw10-z1p-limit-switch-1a-125v-ac-2pcs/
USB Type-C Port: For connecting the device to other peripherals or charging.
https://robu.in/product/usb-3-1-female-socket-type-c-connector-24-pins-breakout-pcb-board/
Connections:
Pro Micro ↔ ESP8266
3/SCL → D1 (ESP8266)
2 → D2 (ESP8266)
GND → GND
VIN → 5V
Additional Connections:
7 → LED DATA
D7 → Down Button
D6 → Up Button
D5 → OK Button
WiFi Deauther Functionality:
The primary purpose of the WiFi Deauther is to deauthenticate devices from WiFi networks. It exploits a vulnerability in the 802.11 WiFi protocol, which allows it to send deauthentication frames to a router. These frames trick the router into believing that a connected device has been disconnected, which interrupts the device’s connection to the network.
This type of attack is useful for:
Testing the security of WiFi networks to identify vulnerabilities.
Demonstrating how denial of service (DoS) attacks can be executed on WiFi networks.
Highlighting how insecure or unprotected networks can easily be targeted.
The attack is carried out by the ESP8266 board using its WiFi capabilities, and the OLED display provides real-time feedback on network selection and attack execution. It’s important to note that such attacks are illegal on networks without permission and should only be used in a controlled environment for educational or testing purposes.
WiFi Duck Functionality:
The WiFi Duck adds another layer of functionality. When connected to a laptop or another device via USB, it acts as a Human Interface Device (HID), such as a keyboard or mouse. Once a laptop is connected to the WiFi hotspot created by the ESP8266, you can send scripts or commands to the laptop remotely, simulating keystrokes or mouse movements.
This works by:
Connecting the WiFi Duck to the target laptop via USB.
Creating a WiFi hotspot using the ESP8266, which the attacker connects to.
Executing scripts that control the laptop’s keyboard, allowing you to automate tasks, inject commands, or potentially deliver payloads.
The real power of the WiFi Duck lies in its ability to go undetected by security software. Since the device emulates a legitimate HID, most antivirus programs don’t flag it as malicious, making it a stealthy tool for executing attacks or testing device security.
Use Cases and Testing:
While testing the WiFi Deauther and WiFi Duck, I was able to:
Deauthenticate multiple devices from a WiFi network, showing how easy it is to disrupt network services.
Control a connected laptop using custom scripts, demonstrating how security flaws can be exploited in seemingly harmless hardware.
Final Thoughts:
The combination of a WiFi Deauther and WiFi Duck presents a powerful toolkit for penetration testers and security enthusiasts. However, it’s crucial to emphasize that these tools should only be used for ethical hacking purposes. If used improperly, they can cause significant disruption and legal issues.
In the end, this project demonstrates how vulnerabilities in common technologies can be exploited and highlights the importance of strengthening WiFi network security through encryption, strong passwords, and regular monitoring for unauthorized access.
5. AIO Server: Turning an Old HP Laptop into a Multi-OS Virtualization Platform
Objective: